![[KDLP] logo](https://kdlp.underground.software/images/kdlp_logo.png)
Listen to the sound of a race condition and understand the fix
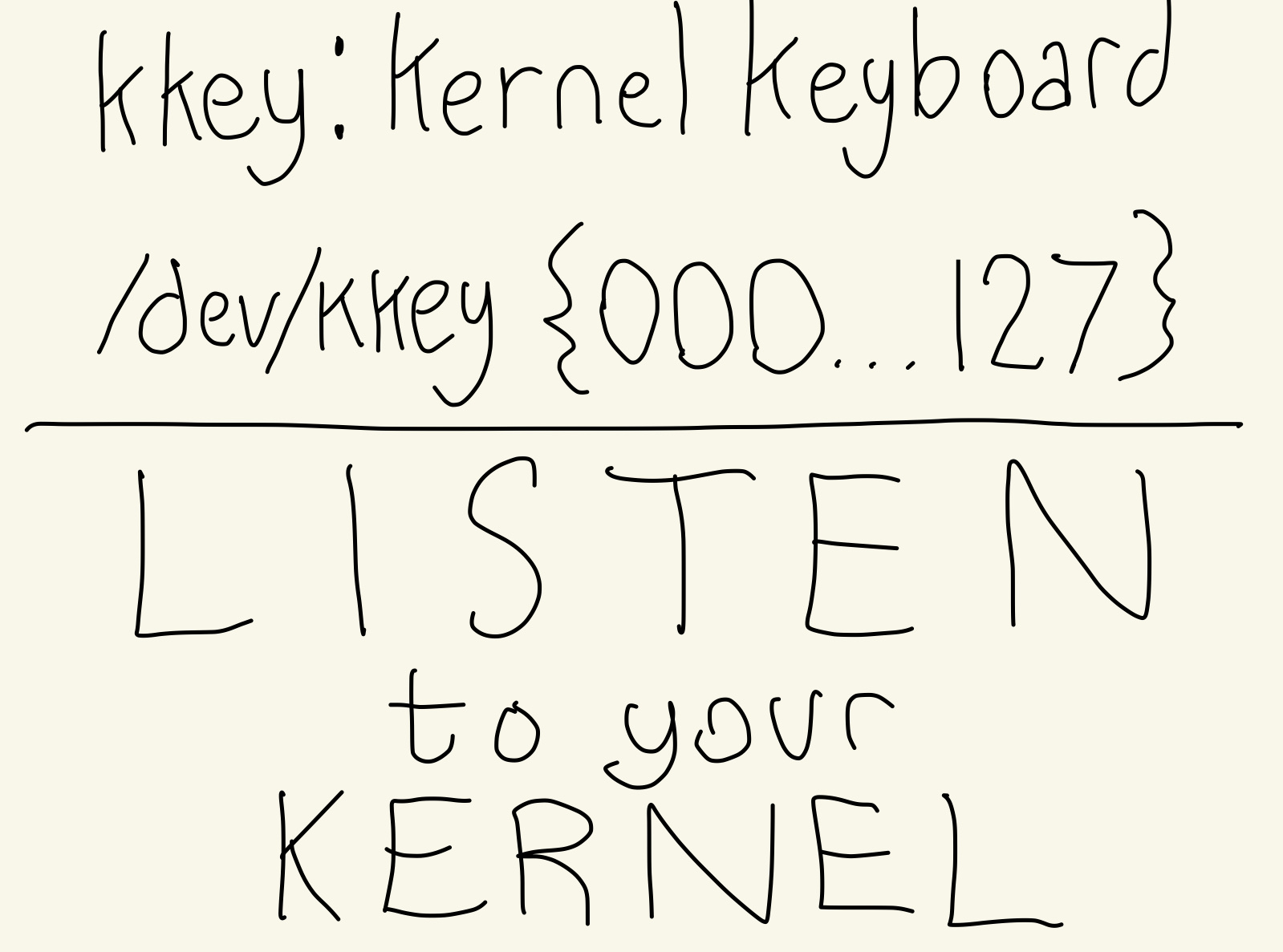
Class files in sysfs
Mutexes in the kernel
Atomic types in the kernel
Triggering a race
Preventing the race
Use sysfs to expose a kernel interface
Can be read-only, write-only, or read-write
More options exist beyond class files
->show() == read
->store() == write
*_from_user?kkey implements RW attributes for velocity and slowdown
Initialization can be static or dynamic
Static: #define DEFINE_MUTEX()
Dynamic: mutex_init()
Destruction is a no-op on unless debugging:
Normal: mutex_destroy()
Debug: mutex_destroy()
Where are these locks forbidden?
Atomic context certain: spin_lock() and spin_unlock()
Maybe atomic context: spin_lock_irqsave()
and spin_unlock_irqrestore()
Initialize with
atomic{,64}_t and ATOMIC_INIT()
Read with
atomic_read() or atomic64_read()
Set with
atomic_set() or atomic64_set()
Also: atomic_long_t and atomic_ptr_t
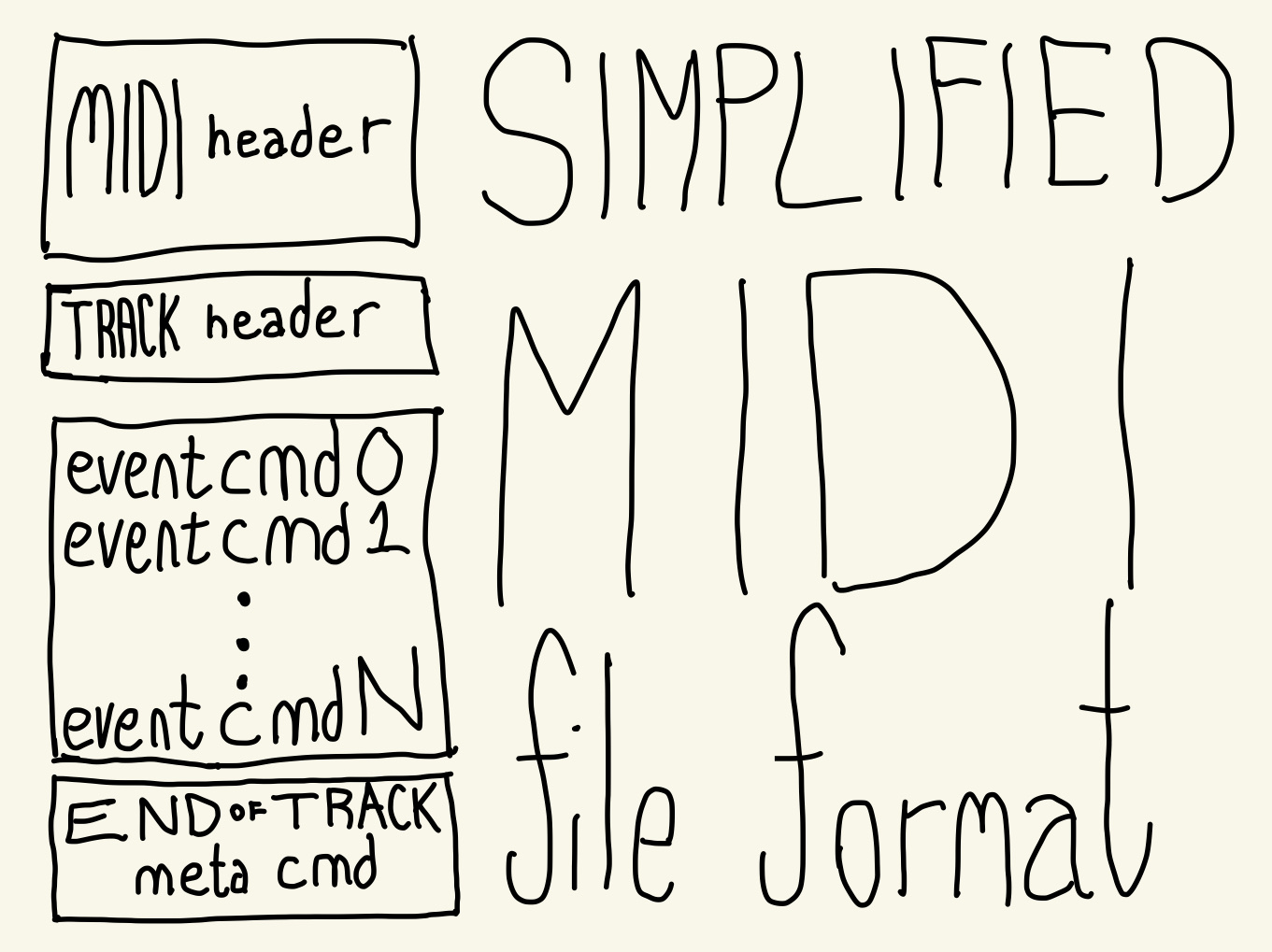
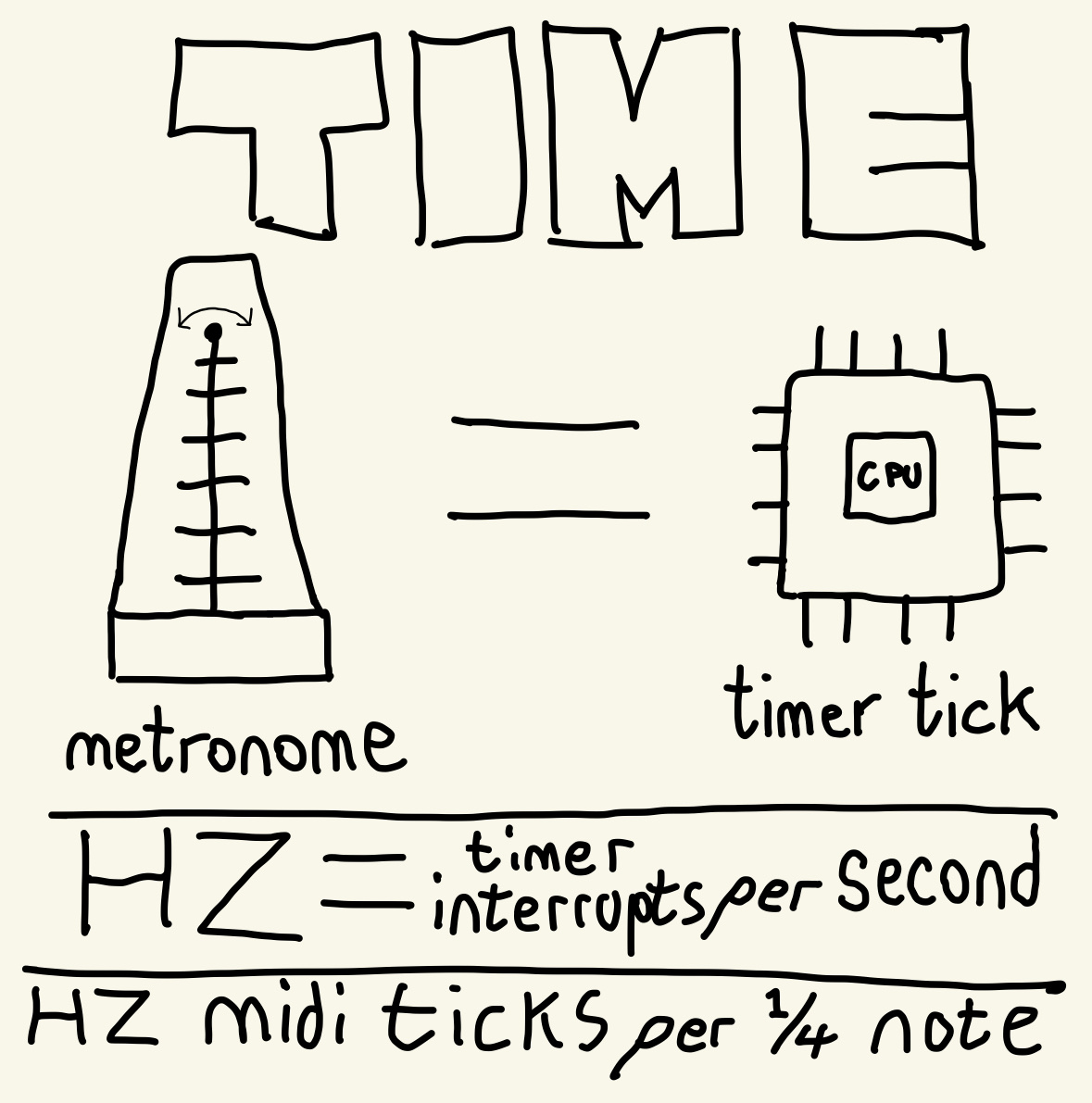
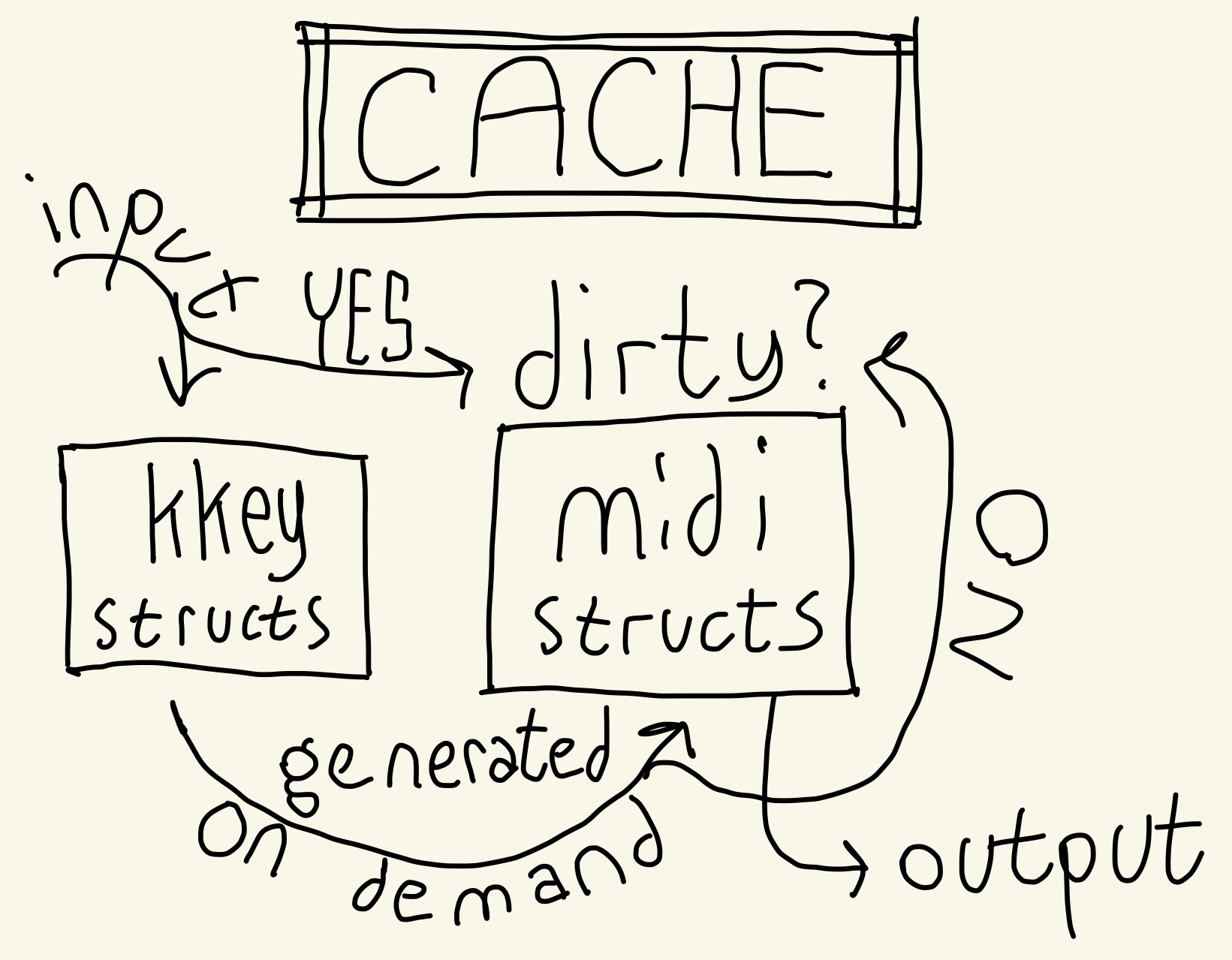
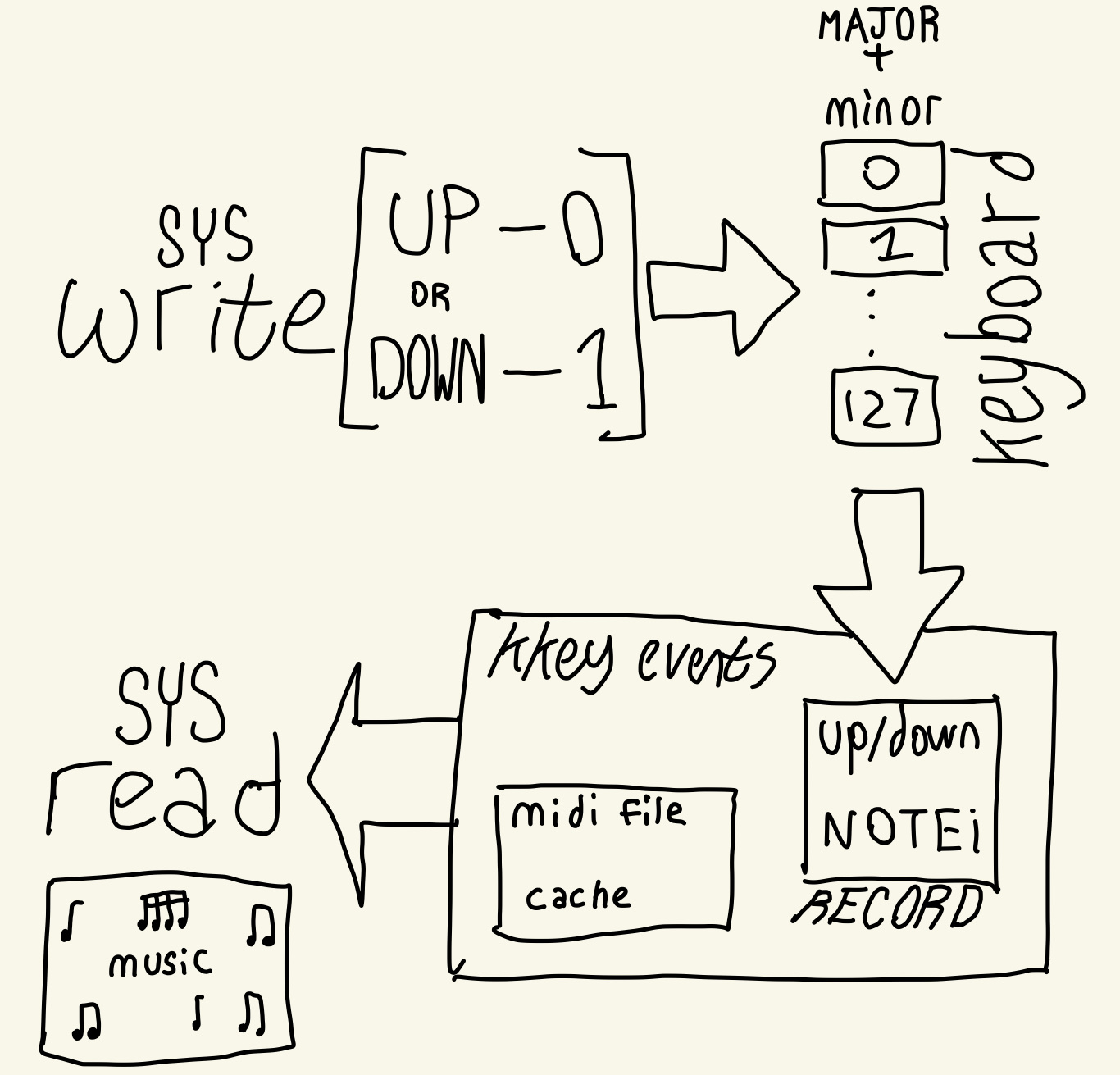
Two processes writing to kkey
Each note is pressed and released
Race condition: a release or press is missing
A press without release will linger
Ensure real multiprocessing
sysconf(3), _SC_NPROCESSORS_ONLN
Can you fix this race?
sysfs can provide a nice API to set/get values in the kernel
Race conditions in the kernel can be subtle and severe
Utilize the appropriate lock type for your use case
Never sleep or block in atomic context!
msg = (silence)whoami = Nonesingularity v0.6-56-g8e52bc8 https://github.com/underground-software/singularity